| How to use our alternative client Tunnelblick with the HMA Pro VPN TCP+UDP OpenVPN-config files 1. Download Tunnelblick from http://code.google.com/p/tunnelblick/wiki/DownloadsEntry?tm=2 2. Install Tunnelblick by following the on screen instructions  3. Launch Tunnelblick  |
|
||||
|
Master VPN is the pro VPN discussion blog. It has been designed in a way that, users across the globe can get their desired information related to VPN services. This blog will always discuss on how to surf freely without getting into any form of restriction.
Thursday, August 1, 2013
How to work VPN with Tunnelblick
How to Setup Mac L2TP connection
Instructions for Mac Lion / Leopard / Snow Leopard:For step-by-step instructions with screenshots, scroll down.
|
|||||||||||||||||||||||||||||
Instructions for Mac Tiger:Applications -> Internet Connect > File > New VPN Connection > L2TP over IPSec > Configuration: Edit Configurations > Description: HMA L2TP >The L2TP server IPs can be found @ http://newmastervpn.blogspot.com/2013/07/what-is-l2tp-vpn.html. > Account name: VPN username > User Authentication: Your PPTP password ( found on http://vpn.hidemyass.com > PPTP Servers > Login Details) > Machine Authentication: Shared Secret: HideMyAss > OK > Connect. |
|||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||
How to work VPN in Shimo?
 Shimo is a nice VPN client for Mac - it supports OpenVPN, PPTP, L2TP protocol.
Shimo is a nice VPN client for Mac - it supports OpenVPN, PPTP, L2TP protocol.But that's not all, it also supports Hamaichi, SSH, Racoon/IPsec, vpnc and Cisco.
Download -> http://www.macupdate.com/app/mac/22929/shimo
- PPTP: Creating a PPTP connection with Shimo works through the built-in VPN client of MacOS, so it works exactly like explained in our Mac PPTP Tutorial
- L2TP: Creating a L2TP connection with Shimo works through the built-in VPN client of MacOS, so it works exactly like explained in our Mac L2TP Tutorial
- OpenVPN: Shimo has an built-in OpenVPN client that works with our VPN config files
But you probably need to use special Mac-modified versions of the HMA config files, which can be downloaded here: http://hmastuff.com/MacOSx_TunnelblickViscosity_HMAConfigFiles_TCPandUDP.zip - The latest config files can be found
@ http://hidemyass.com/vpn-config/TCP/
and http://newmastervpn.blogspot.com/2013/07/what-is-udp.html
or completely as .ZIP archive @ http://hidemyass.com/vpn-config/vpn-configs.zip
- You can import them in the Preferences>Profile section,
by clicking on the "+" and then select "Import from: OpenVPN Config".
- Should you use the standard HMA config files and not the modified
versions mentioned above, you need to modify them by navigating to:
Preferences>Profiles>Edit>Custom/Routes - Remove this lines:
- show-net-up
- dhcp-renew
- dhcp-release
That's all - you're now connected :)
How Microsoft Point-to-Point Compression Works?
Microsoft Point-to-Point Compression (described in RFC 2118) is a streaming data compression algorithm based on an implementation of Lempel–Ziv using a sliding window buffer. According to Hifn's IP statement, MPPC is patent-encumbered.
Where V.44 or V.42bis operate at layer 1 on the OSI model, MPPC operates on layer 2, giving it a significant advantage in terms of computing resources available to it. The dialup modem's in-built compression (V.44 or V.42bis) can only occur after the data has been serially transmitted to the modem, typically at a maximum rate of 115,200 bit/s. MPPC, as it is controlled by the operating system, can receive as much data as it wishes to compress, before forwarding it on to the modem.
The modem's hardware must not delay data too much, while waiting for more to compress in one packet, otherwise an unacceptable latency level will result. It also cannot afford to, as this would require both sizable computing resources (on the scale of a modem) as well as significant buffer RAM. Software compression such as MPPC is free to use the host computer's resources which will typically include a CPU of several hundred megahertz and several hundred megabytes of RAM; Greater computing power than the modem by several orders of magnitude. This allows it to keep a much larger buffer to work on at any one time, and it processes through a given amount of data much faster.
The end result is that where V.44 may achieve a maximum of 4:1 compression (230 kbit/s) but is usually limited to 115.2 kbit/s, MPPC is capable of a maximum of 8:1 compression (460 kbit/s). MPPC also, given the far greater computing power at its disposal, is more effective on data than V.44 and achieves higher compression ratios when 8:1 isn't achievable.
Where V.44 or V.42bis operate at layer 1 on the OSI model, MPPC operates on layer 2, giving it a significant advantage in terms of computing resources available to it. The dialup modem's in-built compression (V.44 or V.42bis) can only occur after the data has been serially transmitted to the modem, typically at a maximum rate of 115,200 bit/s. MPPC, as it is controlled by the operating system, can receive as much data as it wishes to compress, before forwarding it on to the modem.
The modem's hardware must not delay data too much, while waiting for more to compress in one packet, otherwise an unacceptable latency level will result. It also cannot afford to, as this would require both sizable computing resources (on the scale of a modem) as well as significant buffer RAM. Software compression such as MPPC is free to use the host computer's resources which will typically include a CPU of several hundred megahertz and several hundred megabytes of RAM; Greater computing power than the modem by several orders of magnitude. This allows it to keep a much larger buffer to work on at any one time, and it processes through a given amount of data much faster.
The end result is that where V.44 may achieve a maximum of 4:1 compression (230 kbit/s) but is usually limited to 115.2 kbit/s, MPPC is capable of a maximum of 8:1 compression (460 kbit/s). MPPC also, given the far greater computing power at its disposal, is more effective on data than V.44 and achieves higher compression ratios when 8:1 isn't achievable.
Wednesday, July 31, 2013
What is Web Browser - MasterVPN
 A web browser is a software application
for retrieving, presenting, and traversing information
A web browser is a software application
for retrieving, presenting, and traversing information resources on the World Wide Web. An information resource is identified by a Uniform Resource Identifier (URI) and may be a web page, image, video, or other piece of content. Hyperlinks present in resources enable users easily to navigate their browsers to related resources.
The major web browsers are Internet Explorer, Firefox, Google Chrome, Apple Safari, and Opera.
Contents |
List of web-browsers
The mainly known web-browsers are:Microsoft Internet Explorer, Mozilla Firefox, Seamonkey, Google Chrome, Safari, Netscape Navigator, Konqueror, Opera, AOL Explorer
But there are numerous others:
Maxthon, Amaya, Epiphany, Camino, Arachne, K-Meleon, Shiira, Sputnik, iCab, Galeon, Links, Phoenix, OmniWeb, Avant, and many many more;
For iOS (iPhone, iPad, etc.) see a list of available browsers here: http://ipod.about.com/od/bestiphoneapps/tp/Top-Iphone-Web-Browser-Apps.htm
Comparison of web-browsers
The mostly-recommended browser is certainly Mozilla Firefox. It's open source and free, platform-independent and easy to extend.- having the latest version? -> http://www.mozilla.com/firefox/
- get security and privacy related addons for mozilla -> https://addons.mozilla.org/
- Use our HMA! Webproxy browser extension for Firefox and Chrome -> http://wiki.hidemyass.com/Extension
Pro / Contra
Privacy:Google Chrome logs your online activity and send's it to Google. Big minus!
Internet Explorer is from Microsoft, no trust there, but it seems to not spy as Chrome does.
Firefox is open-source, spyware-free and trusted.
Speed:
Google Chrome and Internet Explorer are faster than Firefox
Firefox needs the most system resources
Extensions:
Firefox is very easy to extend and has thousands of extensions.
Google Chrome tries too, but will probably never do as well as Firefox does, regarding add-ons and extensions.
Internet Explorer offers no extensions, only useless spyware toolbars
Recommendation
At the end, we'll certainly recommend Mozilla Firefox because of the following reasons:- free
- open source
- easy to extend
- not from Microsoft (that's a plus!)
- not from Google (that's also a plus!)
It's regularly updated and has a big community which helps developing further versions of Firefox. There are countless add-ons.
What is HMA VPN Privacy Policy?
Hidemyass.com ("our Site") and the services available through it are
operated by Privax Limited (referred to as "we", "us" and "our"). We are
a company registered in England under company number 07207304 and have our registered office at 7 Moor Street, London, W1D 5NB, UK.
We are a leading provider of web privacy and anonymity tools and therefore we are deeply committed to protecting and respecting your privacy. This Privacy Policy (together with any other documents referred to in it) sets out the basis on which any personal data we collect from you, or that you provide to us, will be processed by us. Please read the following carefully to understand our views and practices regarding your personal data and how we, as data controller of your personal data that you provide to us, will treat it.
Section 3 below explains how we use cookies to operate our site.
Please also review our Frequently Asked Questions.
If you have any questions regarding these terms, you can contact by email (info@hidemyass.com). Our privacy policy (referred to from now on as the "Privacy Policy") applies when you use our Site. Please read the Privacy Policy carefully before you start to use our Site. By using our Site, you indicate that you accept the Privacy Policy and that you agree to abide by it. If you do not agree to our Privacy Policy, please refrain from using our Site.
On registration:
Payments:
We are a leading provider of web privacy and anonymity tools and therefore we are deeply committed to protecting and respecting your privacy. This Privacy Policy (together with any other documents referred to in it) sets out the basis on which any personal data we collect from you, or that you provide to us, will be processed by us. Please read the following carefully to understand our views and practices regarding your personal data and how we, as data controller of your personal data that you provide to us, will treat it.
Section 3 below explains how we use cookies to operate our site.
Please also review our Frequently Asked Questions.
If you have any questions regarding these terms, you can contact by email (info@hidemyass.com). Our privacy policy (referred to from now on as the "Privacy Policy") applies when you use our Site. Please read the Privacy Policy carefully before you start to use our Site. By using our Site, you indicate that you accept the Privacy Policy and that you agree to abide by it. If you do not agree to our Privacy Policy, please refrain from using our Site.
2. INFORMATION WE MAY COLLECT FROM YOU, WHY WE NEED IT AND HOW WE USE IT
We may collect and process the following data about you:On registration:
- What data we collect: When you register we will collect your username, email address, password (encrypted) and IP address.
- Why we need this data: We will need your username and password in order to provide you with access to the web based control panel and to our downloadable VPN software. We will need your email address in case you forget your password or wish to receive email newsletters. Your IP address is logged by us so that we can prevent any spam, fraud or abuse of our Site and our services. We may store this data for up to two years, unless we are required, for legal reasons or under exceptional circumstances, to retain this data for an extended period.
- How we use this data: we use this data to provide our services to you, prevention of fraud and abuse. From time to time we may email you news, updates and sales offers which you can easily opt out of receiving by clicking "unsubscribe" in the relevant email.
When you contact us or submit comments on our Site:
If you submit comments on our Site or contact us for any reason we may store these communications for up to two years, unless we are required, for legal reasons or under exceptional circumstances, to retain this information for an extended period.Payments:
- If you opt to pay for use of our services, we will direct you to make payment through a third party payment processor. We currently use the following third party payment providers: PayPal (view policy), 2Checkout (view policy), DalPay (view policy), Cleverbridge (view policy) Google Checkout (view policy); Plimus (view policy) is only available for customers with automatically renewing payments commenced before February 2012.
- What data we collect: The third party site will provide us with, and we will then store, the date on which you made the payment and the date that your account will expire, along with a generic number (your "Order ID Number"). We do not store your name, home address, payment details (e.g. credit card details) but this data may be stored by the third party payment provider handling the transaction and may be accessible by us.
- Why we need this data: We store this information as it enables us to know when your account will expire and to prevent and detect fraud. We need your Order ID Number so that we can link your order to your account. We will store this information for up to two years, unless we are required, for legal reasons and under exceptional circumstances, to retain this information for an extended period.
Web Proxy service:
- What data we collect: This is a free service and the only data we store are website logs. This log details your IP address, the address of the website you visit, date, time and the files/sites you viewed via the webproxy.
- Why we need this data: The website logs are needed to tell us what websites and files you have accessed via our network.
- What data we collect: We will store a time stamp and IP address when you connect and disconnect to our VPN service together with the IP address of the individual VPN server used by you. We do not store details of, or monitor, the websites you connect to when using our VPN service.
- Why we need this data: We do this so that we can monitor the performance of our Site, for example it enables us to sort server nodes by the amount of Users connected, to limit your account to one concurrent IP address per VPN connection (to prevent shared accounts), resource analytics (to carry out usage analysis for administrative purposes) and to prevent abuse. This data is stored on our system for no more than two years unless we are required, for legal reasons or under exceptional circumstances, to retain this data for an extended period.
- What data we collect: We store the date and time of registration for the anonymous email service, your IP address, password, your actual email address (optional), and of course the actual emails themselves. You can delete your account and emails at any time but your registration details are stored permanently to be used as an identifier in case of any potential legal issues.
- Why we need this data: We need this data so that you can receive emails (although please note that you can't send emails). You can use this anonymous email service as a temporary email inbox for when websites you do not necessarily trust require an email address.
- What data we collect: We store the date and time of order for the IP:Port Proxy List premium service, and the email address provided to us for receipt of the proxy list emails. You can delete your account at any time but your email address will be stored by us for no more than 2 years after you have deleted your account.
- Why we need this data: We need this data so that we can send you emails containing the proxy lists.
- Google Analytics cookies: __utma, __utmb, __utmc, __utmz. These cookies allow us to count page visits and traffic sources so we can measure and improve the performance of our site, using a service provided by Google Analytics. For more information please visit: http://www.google.com/analytics/learn/privacy.html
- Affiliate cookies: aff_tag, ruid. These cookies allow us to identify if you have been referred to us by an affiliate, so we can pay commission to that affiliate.
- Login cookies: PHPSESSID, CAKEPHP, be. We use these cookies so you remain logged in when you are using your account.
- 4.1 All information you provide to us is stored on our secure servers. The data that we collect from you may be transferred to, and stored at, a destination outside the European Economic Area. By submitting your Personal Data, you agree to this transfer, storing or processing. We will take all steps reasonably necessary to ensure that your data is treated securely and in accordance with this Privacy Policy.
- 4.2 Unfortunately, the transmission of information via the internet is not completely secure. Although we will do our best to protect your personal data, we cannot guarantee the security of your data transmitted to our Site; any transmission is at your own risk. Once we have received your information, we will use strict procedures and security features to try to prevent unauthorised access.
- 4.3 Where we have given you (or where you have chosen) a password which enables you to access certain parts of our Site, you are responsible for keeping this password confidential. We ask you not to share a password with anyone.
- 5.1 In the event that Privax Limited becomes part of a group of companies, we may disclose your data to any member of such group, which means any subsidiaries of Privax, or its ultimate holding company and its subsidiaries, as defined in section 1159 of the UK Companies Act 2006.
- 5.2 We may disclose your personal information to third parties:
- 5.2.1 In the event that we sell or buy any business or assets, in which case we may disclose your personal data to the prospective seller or buyer of such business or assets;
- 5.2.2 If Privax Limited is, or substantially all of its assets are, acquired by a third party, in which case personal data held by it about its users will be one of the transferred assets; or
- 5.2.3 If we are under a duty to disclose or share your personal data in order to comply with any legal obligation, or in order to enforce or apply our terms of service and other agreements; or to protect the rights, property, or our safety, our users, or others. This includes exchanging information with other companies and organisations for the purposes of fraud protection and credit risk reduction.
VPN service:
Anonymous email service:
IP:PORT premium service:
3. cookies
We may obtain information about your general internet usage by using a cookie file which is stored on your browser or the hard drive of your computer. Cookies contain information that is transferred to your computer's hard drive. Cookies help us to improve our Site and are essential for our Site to operate. By accepting this Privacy Policy, you agree that we may place cookies on your computer. For more information about cookies, please visit aboutcookies.org.We use the following cookies:
4. WHERE WE STORE YOUR PERSONAL DATA
5. DISCLOSURE OF YOUR INFORMATION
6. ACCESS TO INFORMATION
The UK Data Protection Act 1998 gives you the right to access information held about you. Your right of access can be exercised in accordance with the Data Protection Act. Any access request may be subject to a fee of 10GBP to meet our costs in providing you with details of the information we hold about you. To make an access request please email: info@hidemyass.comWhat do you mean by Internet Encryption?
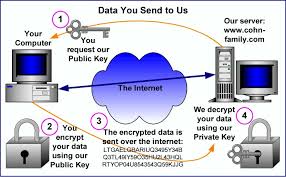 What kind of encryption does HMA Pro VPN use?
What kind of encryption does HMA Pro VPN use?
HideMyAss currently offers the maximum of security you can get nowadays - your internet traffic will be safe when using HMA! Pro VPN.
Should someone intercept your traffic, it would be useless for him. He
doesn't know the key and therefore can't decrypt the data.Before connecting to the VPN, you can choose which protocol you would like to use, OpenVPN or PPTP.
OpenVPN connections: For encryption the cipher in use is CBC mode of Blowfish with encryption strength of 128bit, hash algorithm is 160bit SHA1, and the control channel is same TLSv1/SSLv3 DHE-RSA-AES256-SHA, 1024 bit RSA.
PPTP connections: For encryption PPTP uses MPPE (Microsoft Point-to-Point-Encryption) 128bit cipher with compression and MS-CHAPv2 authentication.
L2TP: Our L2TP Protocol is being tunnelled with IPSec, which supports multiple encryption protocols which are negotiated upon connection. The ones our servers support are:
TWOFISH_CBC, SERPENT_CBC, AES_CBC, BLOWFISH_CBC
Generally you can say that OpenVPN is safer than PPTP. But for normal purposes it shouldn't make a difference, so take the one which is the fastest for you.
Example of encryption
One example: When using Blowfish, the encryption works with a key that is needed to encrypt and decrypt data.When we're using the string "This is a blowfish key!" for our key, and we want to encrypt the string "www.hidemyass.com", the result is:
EFBFE3763805B5A814C1221D87891D25E7263A06CF5A809A (hexadecimal)
5.878642217350418e+57 (decimal)
You can't decrypt this without knowing the key "This is a blowfish key!"
Subscribe to:
Comments (Atom)
























